Accelerate Success with AI-Powered Test Automation – Smarter, Faster, Flawless
Start free trialHow secure is your software? Is it susceptible to unwarranted intrusion, thus exposing sensitive data and compute capacity to the outside world?
These questions are pertinent to every software development and testing team. Besides validating the functionality and testing the performance of any software system, it is extremely important to secure the software’s integrity from any potential threats. Security testing identifies any vulnerabilities that may expose software to external threats. It also identifies defects that could result in loss of sensitive information or revenue, which may impact the reputation of the organization.
Key Attributes of Security Testing
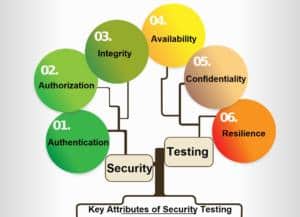
For security testing to be effective, it has to start early in the software development stage and continue throughout the development cycle till deployment. There are certain key attributes which are generally tested for any software system.These are indicative attributes. Not one size fits all, hence security test cases are customized based on the end purpose of the software.
Quick Glance at Types of Security Testing
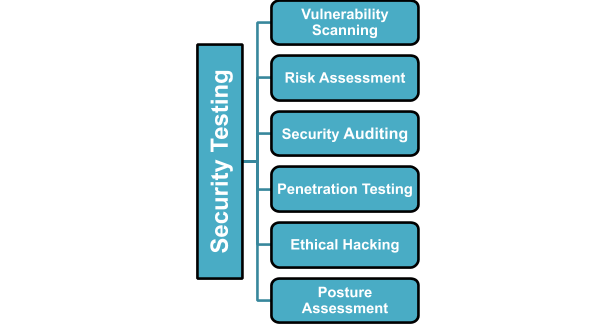
- Vulnerability scanning is an automated process that involves scanning and detecting potential weak points of software against known vulnerability signatures.
- Risk assessment identifies and assesses threats to the security of any system. It then attaches priorities to those risks – low, medium, high.
- Security Auditing is a process to identify flaws in the system’s configuration, network, operating environment, interfaces etc. Security audit report should have a comprehensive list of past and potential threats to the system.
- Penetration testing involves simulation of an external hacking attempt to spot any potential security loopholes which may expose the system to any breaches.
- Ethical hacking is done by a white hat hacker with sole intention of exposing security flaws which can be exploited by people with malicious intent.
- Posture assessment is a custom blend of vulnerability scanning, ethical hacking and risk assessment.

Accentuating Benefits of Security Testing With Continuous Regression

Introduction of Security regression testing in an existing QA framework significantly improves software’s test coverage, thereby resulting in a much more secure and therefore higher quality system.
Security testing needs the support of regression testing to ensure that no functionality was broken while fixing security related bugs. It also works the other way round. Fixing bugs may result in security gaps, which need to be taken care of on priority.
Regression testing ensures that any code changes does not introduce defects, which lead to a malfunctioning software. Regression testing is largely focused on functional and performance aspect of software. But it is equally important to consider the security risks that might have been accidentally introduced due to code modifications.
This is extremely crucial at deployment and delivery stage, when the software is ready to showcase its functions with perfection.
Testers need to understand the concepts of security threat modelling in order to write detailed security related regression test cases.
There are many commercial and free, open-source tools available in the market for assisting in and automating security regression testing, OS, library, application and web vulnerability scanning can be fully automated with tools like Nessus, Metasploit and Burp Suite. These security tools can be integrated into a CI/CD pipeline. Static code analysis, or source code analysis, can be fully automated with tools like Find Security Bugs, Fortify and Klocwork.
By embedding automated security tests in development cycle ensures faster delivery of software by enabling the teams to have an instant feedback to act on. These tests can be conducted with repeated consistency.
Penetration testing plays a very important role in security testing. It is primarily a manual activity by security experts, but supported by tools, frameworks and scripts. The tester spends a significant amount of time in scrutinizing and analyzing the software to unearth any deep-rooted flaw, which may otherwise go unnoticed at surface level.
What if security testing is postponed for the last minute and a major issue is detected just before final deployment? Tracing back to the origin of bug and fixing will have serious time related and monetary repercussions, if done much later. This is precisely the reason security testing should be included in regression cycles.
Many organizations choose to automate what they can, e.g. vulnerability scanning and static code analysis, and schedule the more costly threat model updates and penetration testing for major releases or regular intervals, e.g. quarterly.
Conclusion
The world of software development is an evolving phenomenon with growing dependence on digital channels for day to day functioning, be it personal or business. With this, security attacks have increased exponentially. In such a scenario, it is vital that software development organizations give high importance to security testing. Investing time and effort in security audits to identify potential loopholes and developing testing strategy helps in building a high quality product. A comprehensive security regression process analyzes and evaluates all the layers of software to identify and expose any chinks in the armor.
Security testing complements Agile and DevOps approaches, which encourage frequent code changes, deployments and testing. Introducing security testing as part of regression test exponentially improves the quality of product. Since, security threats, if any, are remediated with every software change, it becomes much easier for all stakeholders. Any security risk discovered much later in the development cycle proves costly, because backtracking and fixing requires time and resources. In order to achieve this, verification at the system level is important. Using your existing system automation, or adding in a service like Webomates CQ for CI/CD can far more quickly and easily help realize the goal of rapid and reliable deployments in the field.
If you are interested in learning more about Webomates’ CQ service please click here and schedule a demo or reach out to us at info@webomates.com.
Tags: Quality Assurance, Regression Testing, Security Threats, Software Testing
Test Smarter, Not Harder: Get Your Free Trial Today!
Start Free Trial
Leave a Reply